Discover the many
Use Cases
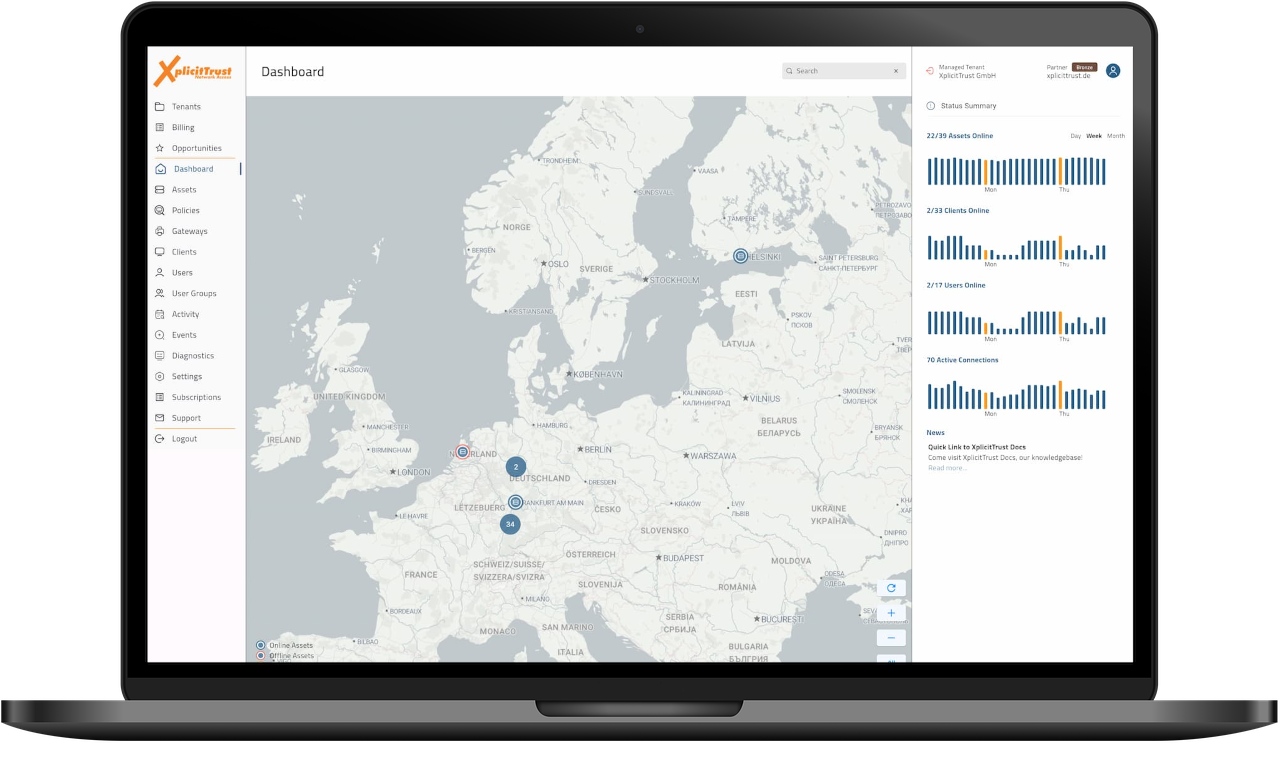
Our customers appreciate the powerful features of XplicitTrust Network Access in a variety of different scenarios. Find out how our innovative technology can help you achieve your goals.
Start your 30-day free trial now. No strings attached. No credit card required.
Sign Up (30 days free trial)